Welcome to AXIOTROP, Your CMMC Partner
Cybersecurity Maturity Model Certification (CMMC)
CMMC is essential for businesses seeking to participate in DoW contracts, ensuring that they are capable of protecting United States national defense information and defending against cyber threats and maintaining the highest standards of information security.
By achieving CMMC, companies not only comply with DoW requirements but also demonstrate their commitment to national security, maintaining the integrity of the supply chain, and protecting our war fighters.
CMMC History
2010
-
Executive Order (EO) 13556, "Controlled Unclassified Information" (CUI) program established.
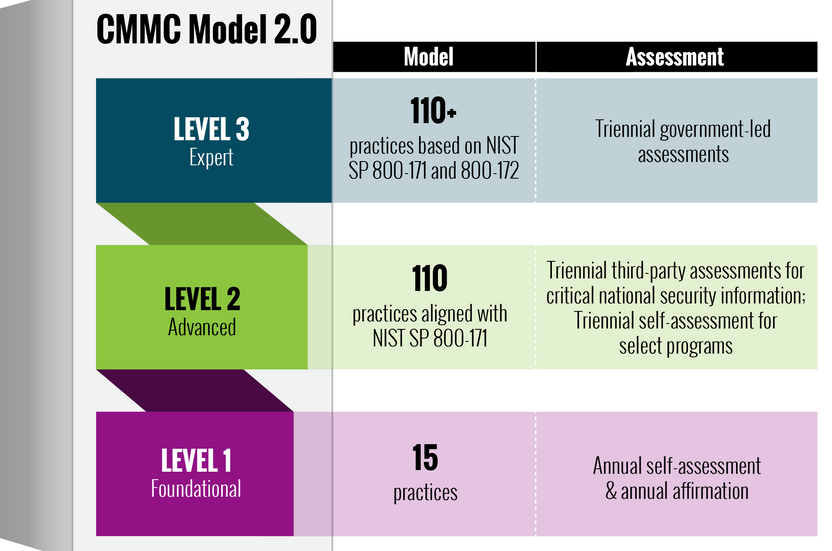
CMMC 2.0
The CMMC 2.0 model has been streamlined to three levels, aligning its requirements with the NIST SP 800-171 and NIST SP 800-172 standards.
The assessment process has been revised, with limited use of Plans of Action and Milestones (POA&Ms) and time-bound waivers requiring senior DoW approval.
Level 1 DIB contractors are allowed to self-assess their cybersecurity programs and provide an attestation to the DoW.
Most Level 2 and all Level 3 DIB contractors are required to obtain a third party assessment of their cybersecurity program.

AXIOTROP Webinars
AXIOTROP has had the opportunity to participate in these insightful webinars, providing valuable knowledge and engaging with industry experts. Explore the webinars and discover key takeaways that will support your CMMC journey!
Included below is a webinar series dedicated to CMMC education. Hosted by RIMA, featuring AXIOTROP
CMMC Client Testimonials
AXIOTROP Blogs


Phase 1 is Here: CMMC Compliance is Now a Mandatory Checkpoint


The CMMC Readiness Reality


What is the POA&M Process for Final CMMC Certification?


How CMMC Level 2 Certification Strengthens Your Place as a Trusted Partner


Proactive CMMC Compliance for the DoD Supply Chain


The CMMC Countdown is Over: What Every DoD Contractor Needs to Know NOW


Understanding Identification & Authentication














Securing Business Success with System & Information Integrity Domain


Understanding the Critical Role of Communications Protection in Safeguarding


Stop Procrastinating – Essential CMMC Awareness Workshop



CMMC Is Taking Effect: What DoD Contractors Can Expect in 2025



Understanding Personnel Security in NIST SP 800-171r2


CMMC Budgeting 101: What Every Defense Contractor Should Know


CMMC – a long time in the making…


Virtru's CMMC Compass Series Webinar features Joe Devine


AXIOTROP Celebrates Winning PBN 2024 Manufacturing Awards


The Hidden Risks of Inflated SPRS Scores, Why Accuracy Matters for Government Contracts


Boosting Your SPRS Score: Key Steps to Strengthen Cybersecurity Compliance and Win Contracts


Decoding SPRS Scores for Compliance for Defense Contractors


Understanding DOD CMMC Level 2 vs. Level 1


DIB Rulemaking Update (Q4)


Understanding the CMMC Rules: What’s the Difference Between Title 32 and Title 48?


Revenue hit from a cyber breach - don’t let this happen to you!


Cyber Hijacking of a Yogurt Shipment - What Next???


DIB Rulemaking Update (Q2)


Trade & Transportation Cybersecurity Survey – Insights and Recommendations


Breaches Increase Despite Greater Cybersecurity Spending - Why?


Public Comment Period Ending soon for CMMC 2.0


What is a Cybersecurity Assessment and Why Should You Get One?


Cybersecurity Talent – Another Reason to Outsource / Partner with a Highly Qualified Cybersecurity &


CTPAT Added Cybersecurity Criteria to Their Minimum Security Criteria - What Now?


Implications of the National Cybersecurity Strategy for SMB’s


Why it’s Time to Complete an Independent Cybersecurity Assessment


Enterprise Risk Management and Cybersecurity - A Growing Challenge


Why should an MSP consider partnering with a Cybersecurity & Compliance Firm?


eCommerce and Cybersecurity - a Risky Mixture?


The Cybersecurity Talent Gap is Widening - Is “Renting” Your Best Alternative?

CMMC 2.0 Is on Its Way - Here's What You Need to Know


AXIOTROP Attains CMMC Certification for Second Year


Strengthening your Cybersecurity Shouldn’t be a Cash Drain


The Key to MSP Growth in 2023? Cybersecurity Expertise


What is NIST? Why use the NIST Cyber Security Framework?


Strengthening Cybersecurity for Competitive Advantage






